Kringle Kiosk⚓︎
Elf: Shinny Upatree
Direct link: shell terminal
Objective: Investigate S3 Bucket
Request⚓︎
Shinny Upatree
Hiya hiya - I'm Shinny Upatree!
Check out this cool KringleCon kiosk!
You can get a map of the castle, learn about where the elves are, and get your own badge printed right on-screen!
Be careful with that last one though. I heard someone say it's "ingestible." Or something...
Do you think you could check and see if there is an issue?
Hints⚓︎
Command Injection
There's probably some kind of command injection vulnerability in the menu terminal.
Solution⚓︎
Welcome message
Welcome to our castle, we're so glad to have you with us!
Come and browse the kiosk; though our app's a bit suspicious.
Poke around, try running bash, please try to come discover,
Need our devs who made our app pull/patch to help recover?
Escape the menu by launching /bin/bash
Press enter to continue...
The objective is to escape the menu and run /bin/bash. Shinny hints at the badge printer being problematic so open that menu option. Completely ignore the warning about special characters and enter a few anyway.
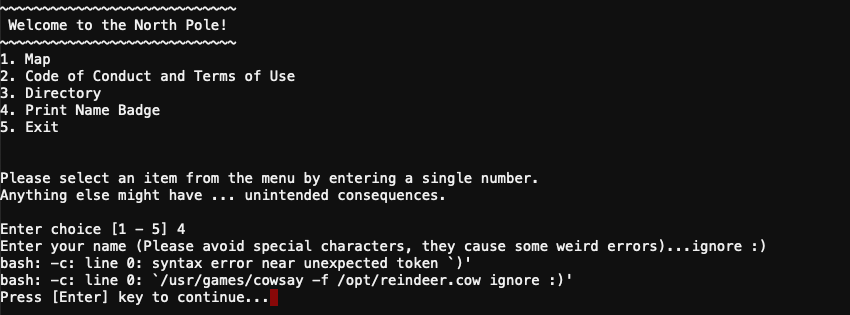
It looks like our text is used unmodified as the input for /usr/games/cowsay. Leverage this command injection vulnerability by adding a ; to the end of the cowsay command followed by /bin/bash as requested in the welcome message.
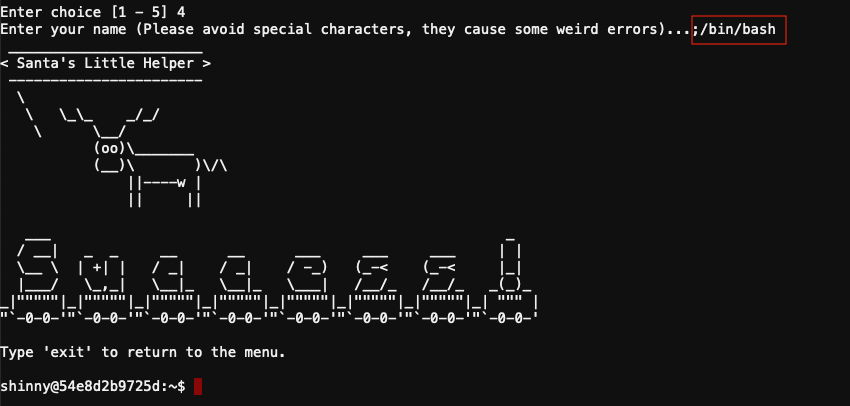
Answer
Enter ;/bin/bash as your badge name.
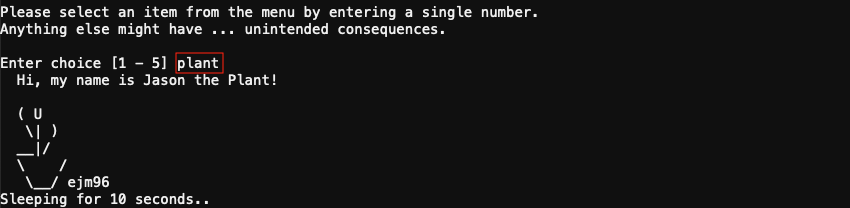
Finding Jason!
The /home/shinny/welcome.sh script contains a hidden plant menu option (line 11) which will display the contents of /opt/plant.txt. There's an additional ASCII image of a mailbox at /opt/mailbox.txt but that file isn't used in the menu script.
1 2 3 4 5 6 7 8 9 10 11 12 13 14 | |
Oh hi, Jason!
Response⚓︎
Shinny Upatree
Golly - wow! You sure found the flaw for us!
Say, we've been having an issue with an Amazon S3 bucket.
Do you think you could help find Santa's package file?
Jeepers, it seems there's always a leaky bucket in the news. You'd think we could find our own files!
Digininja has a great guide, if you're new to S3 searching.
He even released a tool for the task - what a guy!
The package wrapper Santa used is reversible, but it may take you some trying.
Good luck, and thanks for pitching in!