Linux Primer⚓︎
Elf: Sugarplum Mary
Direct link: linux terminal
Objective: Point-of-Sale Password Recovery
Request⚓︎
Sugarplum Mary
Sugarplum Mary? That's me!
I was just playing with this here terminal and learning some Linux!
It's a great intro to the Bash terminal.
If you get stuck at any point, type hintme to get a nudge!
Can you make it to the end?
Solution⚓︎
Welcome message
The North Pole 🍭 Lollipop Maker:
All the lollipops on this system have been stolen by munchkins.
Capture munchkins by following instructions here and 🍭's will appear in the green bar below.
Run the command "hintme" to receive a hint.
Many of the terminals at KringleCon are designed to help you get acquainted with a specific technology or tool. In this case the Bash command shell and some common shell commands. The Answers section below provides a copy/pastable overview of each of the commands. All entries link to explainshell.com which provides a detailed explanation of the command and its parameters.
Answers
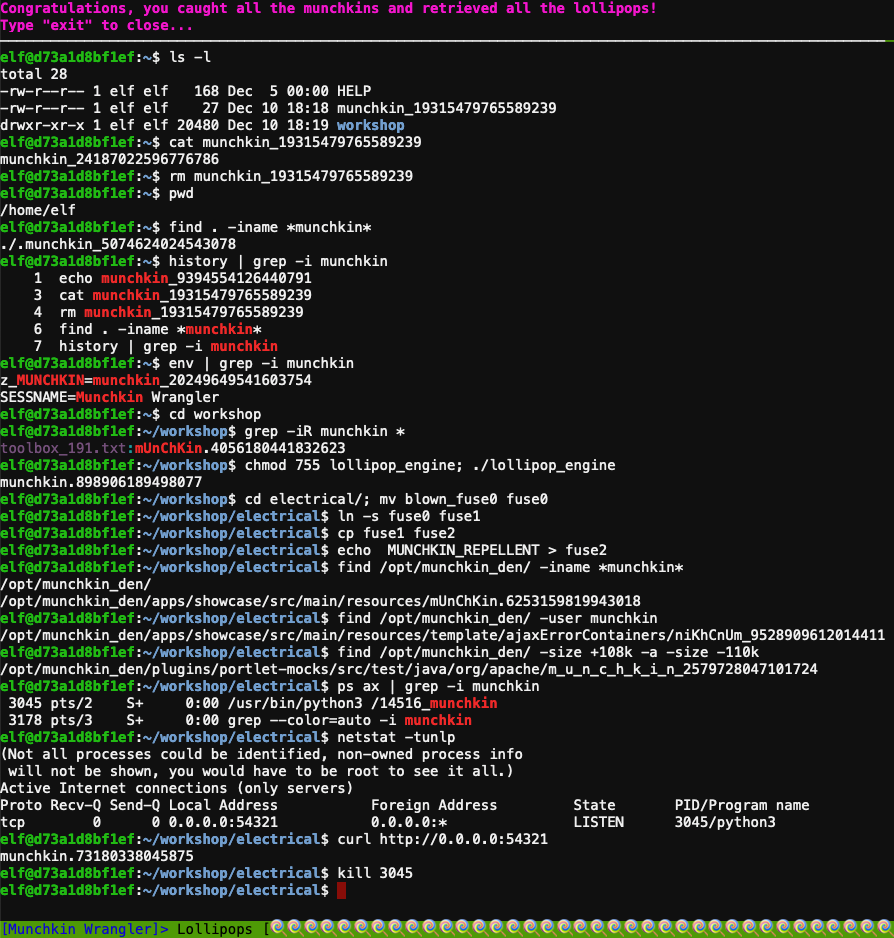
- Perform a directory listing:
ls -l - Find the munchkin inside the munchkin:
cat munchkin_19315479765589239 - Remove the munchkin in your home dir:
rm munchkin_19315479765589239 - Print the present working dir:
pwd - Find the hidden munchkin:
find . -iname *munchkin* - Find the munchkin in your command history:
history | grep -i munchkin - Find the munchkin in your env vars:
env | grep -i munchkin - Head into the workshop:
cd workshop - Find which toolbox the munchkin is in:
grep -iR munchkin * - Run the
lollipop_enginebinary:chmod 755 lollipop_engine; ./lollipop_engine cdinto electrical and renameblown_fuse0tofuse0:cd electrical/; mv blown_fuse0 fuse0- Make a symbolic link named
fuse1that points tofuse0:ln -s fuse0 fuse1 - Make a copy of
fuse1namedfuse2:cp fuse1 fuse2 - Add MUNCHKIN_REPELLENT into the file
fuse2echo MUNCHKIN_REPELLENT > fuse2 - Find the munchkin somewhere in
/opt/munchkin_den:find /opt/munchkin_den/ -iname *munchkin* - Find the file in
/opt/munchkin_denthat is owned by the usermunchkin:find /opt/munchkin_den/ -user munchkin - Find the file created by munchkins >108 Kb and <110 Kb in
/opt/munchkin_den:find /opt/munchkin_den/ -size +108k -a -size -110k - List running processes to find another munchkin:
ps ax | grep -i munchkin - Use a command to have the only listening port display:
netstat -tunlp - Interact with this server to retrieve the last munchkin:
curl http://0.0.0.0:54321 - Stop the
14516_munchkinprocess:kill 3045
Response⚓︎
Sugarplum Mary
You did it - great! Maybe you can help me configure my postfix mail server on Gentoo!
Just kidding!
Hey, wouldja' mind helping me get into my point-of-sale terminal?
It's down, and we kinda' need it running.
Problem is: it is asking for a password. I never set one!
Can you help me figure out what it is so I can get set up?
Shinny says this might be an Electron application.
I hear there's a way to extract an ASAR file from the binary, but I haven't looked into it yet.