Investigate S3 Bucket⚓︎
Difficulty:
Direct link: awsbucket terminal
Terminal hint: Kringle Kiosk
Objective⚓︎
Request
When you unwrap the over-wrapped file, what text string is inside the package? Talk to Shinny Upatree in front of the castle for hints on this challenge.
Shinny Upatree
Say, we've been having an issue with an Amazon S3 bucket.
Do you think you could help find Santa's package file?
Jeepers, it seems there's always a leaky bucket in the news. You'd think we could find our own files!
Digininja has a great guide, if you're new to S3 searching.
He even released a tool for the task - what a guy!
The package wrapper Santa used is reversible, but it may take you some trying.
Good luck, and thanks for pitching in!
Hints⚓︎
Find Santa's Package
Find Santa's package file from the cloud storage provider. Check Josh Wright's talk for more tips!
Santa's Wrapper3000
Santa's Wrapper3000 is pretty buggy. It uses several compression tools, binary to ASCII conversion, and other tools to wrap packages.
Finding S3 Buckets
Robin Wood wrote up a guide about finding these open S3 buckets.
Leaky AWS S3 Buckets
It seems like there's a new story every week about data exposed through unprotected Amazon S3 buckets.
Bucket_finder.rb
He even wrote a tool to search for unprotected buckets!
Solution⚓︎
Updated welcome message
During the event the welcome message displayed when opening the terminal was updated with some additional hints.
Hints: Use the file command to identify a file type. You can also examine
tool help using the man command. Search all man pages for a string such as
a file extension using the apropos command.
To see this help again, run cat /etc/motd.
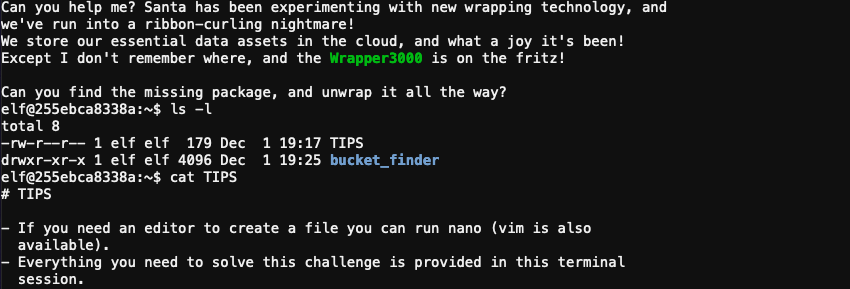
First we need to find the S3 bucket that contains Santa's package file. Navigate to the bucket_finder folder which contains a bucket_finder.rb script and a sample wordlist with some sample bucket names. Running bucket_finder.rb wordlist will find some buckets, but none will be publicly accessible.
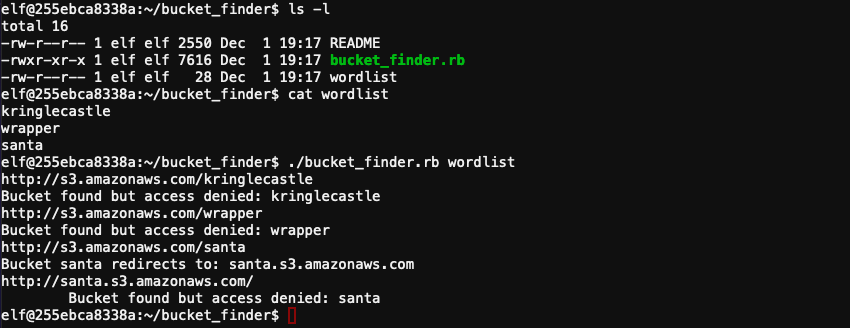
The welcome message displayed when you connect to the terminal highlights the Wrapper3000 string, so add a couple of variations of the word to the wordlist file and execute the command bucket_finder.rb wordlist --download. This not only checks for publicly accessible S3 buckets matching the strings specified in the wordlist file, but also downloads the data.
Be nice!
During the event the bucket_finder.rb script was updated to limit the number of entries in the wordlist to 50.
HO HO HO
The people at AWS are on the nice list this year! You shouldn't use such a long
wordlist. Use the hints in the description for this challenge to help choose a
small wordlist to find the missing bucket! Run 'cat /etc/motd' to see it again.
SANTA
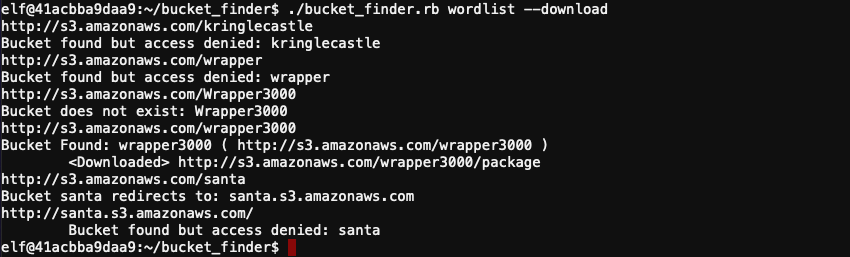
Now that the package file has been downloaded to /home/elf/bucket_finder/wrapper3000/package, we can start the process of unpacking it. We first need to determine the file type though. Run file package which will tell you the contents of the file is ASCII text, with very long lines. cat package will show you the contents.
/home/elf/bucket_finder/wrapper3000/package
UEsDBAoAAAAAAIAwhFEbRT8anwEAAJ8BAAAcABwAcGFja2FnZS50eHQuWi54ei54eGQudGFyLmJ6MlVUCQADoBfKX6AXyl91eAsAAQT2AQAABBQAAA
BCWmg5MUFZJlNZ2ktivwABHv+Q3hASgGSn//AvBxDwf/xe0gQAAAgwAVmkYRTKe1PVM9U0ekMg2poAAAGgPUPUGqehhCMSgaBoAD1NNAAAAyEmJpR5
QGg0bSPU/VA0eo9IaHqBkxw2YZK2NUASOegDIzwMXMHBCFACgIEvQ2Jrg8V50tDjh61Pt3Q8CmgpFFunc1Ipui+SqsYB04M/gWKKc0Vs2DXkzeJmik
tINqjo3JjKAA4dLgLtPN15oADLe80tnfLGXhIWaJMiEeSX992uxodRJ6EAzIFzqSbWtnNqCTEDML9AK7HHSzyyBYKwCFBVJh17T636a6YgyjX0eE0I
sCbjcBkRPgkKz6q0okb1sWicMaky2Mgsqw2nUm5ayPHUeIktnBIvkiUWxYEiRs5nFOM8MTk8SitV7lcxOKst2QedSxZ851ceDQexsLsJ3C89Z/gQ6X
n6KBKqFsKyTkaqO+1FgmImtHKoJkMctd2B9JkcwvMr+hWIEcIQjAZGhSKYNPxHJFqJ3t32Vjgn/OGdQJiIHv4u5IpwoSG0lsV+UEsBAh4DCgAAAAAA
gDCEURtFPxqfAQAAnwEAABwAGAAAAAAAAAAAAKSBAAAAAHBhY2thZ2UudHh0LloueHoueHhkLnRhci5iejJVVAUAA6AXyl91eAsAAQT2AQAABBQAAA
BQSwUGAAAAAAEAAQBiAAAA9QEAAAAA
Looks like we're dealing with BASE64-encoded data which gives us our starting point. Since we can't be sure what the output of the decoded data will be, we will redirect the output to a file instead of the console using cat package | base64 -d > package2. From this point forward we repeat the process of identifying the file format and unpacking.
| # | Input file | File type | Unpack command |
|---|---|---|---|
| 1 | package |
BASE64 | cat package | base64 -d > package2 |
| 2 | package2 |
ZIP archive | unzip package2 |
| 3 | package.txt.Z.xz.xxd.tar.bz2 |
bzip2 archive | bunzip2 package.txt.Z.xz.xxd.tar.bz2 |
| 4 | package.txt.Z.xz.xxd.tar |
tar archive | tar xf package.txt.Z.xz.xxd.tar |
| 5 | package.txt.Z.xz.xxd |
Hex dump | xxd -r package.txt.Z.xz.xxd > package.txt.Z.xz |
| 6 | package.txt.Z.xz |
xz archive | xz -d package.txt.Z.xz |
| 7 | package.txt.Z |
compress'd data | uncompress package.txt.Z |
Finally, after 7 steps, cat package.txt gives us the answer.
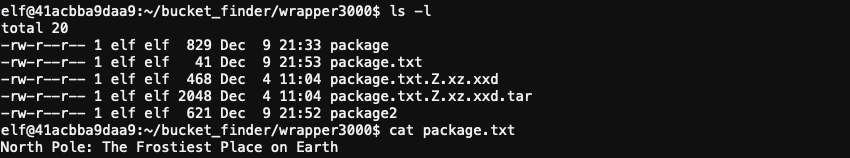
Answer
North Pole: The Frostiest Place on Earth