Speaker UNPrep⚓︎
Elf: Bushy Evergreen
Direct link: speaker terminal
Objective: Open HID Lock
Request⚓︎
Bushy Evergreen
Ohai! Bushy Evergreen, just trying to get this door open.
It's running some Rust code written by Alabaster Snowball.
I'm pretty sure the password I need for ./door is right in the executable itself.
Isn't there a way to view the human-readable strings in a binary file?
Hints⚓︎
Strings in Binary Files
The strings command is common in Linux and available in Windows as part of SysInternals.
Lookup Table
For polyalphabetic ciphers, if you have control over inputs and visibilty of outputs, lookup tables can save the day.
Letting a Program Decrypt for You
While you have to use the lights program in /home/elf/ to turn the lights on, you can delete parts in /home/elf/lab/.
Solution⚓︎
Welcome message
Help us get into the Speaker Unpreparedness Room!
The door is controlled by ./door, but it needs a password! If you can figure
out the password, it'll open the door right up!
Oh, and if you have extra time, maybe you can turn on the lights with ./lights
activate the vending machines with ./vending-machines? Those are a little
trickier, they have configuration files, but it'd help us a lot!
(You can do one now and come back to do the others later if you want)
We copied edit-able versions of everything into the ./lab/ folder, in case you
want to try EDITING or REMOVING the configuration files to see how the binaries
react.
Note: These don't require low-level reverse engineering, so you can put away IDA
and Ghidra (unless you WANT to use them!)
Door
The password is stored in plaintext in the door binary and can be extracted using strings door | grep pass.
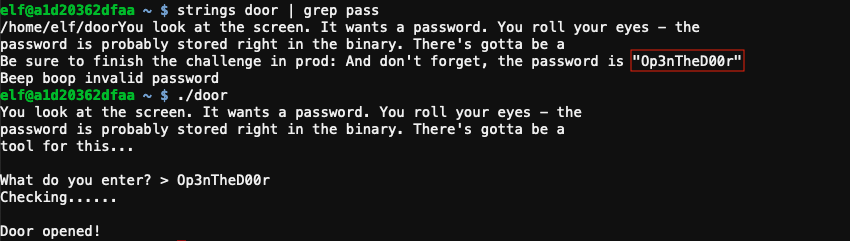
Answer
Op3nTheD00r
Bushy Evergreen
That's it! What a great password...
Oh, this might be a good time to mention another lock in the castle.
Santa asked me to ask you to evaluate the security of our new HID lock.
If ever you find yourself in posession of a Proxmark3, click it in your badge to interact with it.
It's a slick device that can read others' badges!
Lights
Bushy Evergreen
Hey, you want to help me figure out the light switch too? Those come in handy sometimes.
The password we need is in the lights.conf file, but it seems to be encrypted.
There's another instance of the program and configuration in ~/lab/ you can play around with.
What if we set the user name to an encrypted value?
The username and password for the light application are read from the lights.conf configuration file. Any configuration value starting with E$ is considered encrypted and automatically decrypted. To retrieve the password, edit /home/elf/lab/lights.conf and copy the encrypted password into the username field. Running /home/elf/lab/light will now cause the application to decrypt the encrypted username value so it can be shown as part of the welcome message.
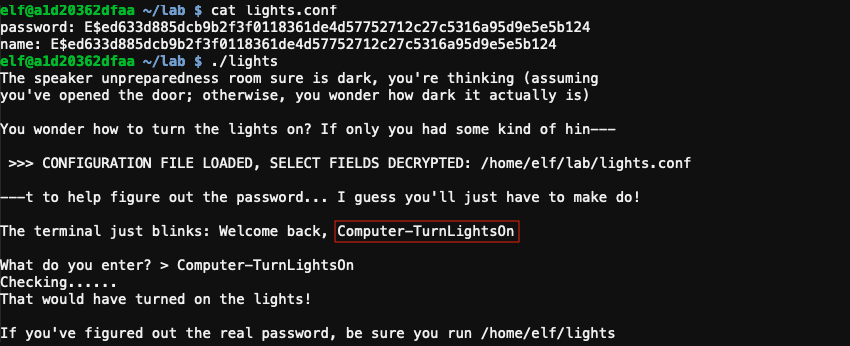
To turn the lights on, use the recovered password with the production version of the app, located at /home/elf/light.
Answer
Computer-TurnLightsOn
Bushy Evergreen
Wow - that worked? I mean, it worked! Hooray for opportunistic decryption, I guess!
Oh, did I mention that the Proxmark can simulate badges? Cool, huh?
There are lots of references online to help.
In fact, there's a talk going on right now!
Vending machine
Bushy Evergreen
So hey, if you want, there's one more challenge.
You see, there's a vending machine in there that the speakers like to use sometimes.
Play around with ./vending_machines in the lab folder.
You know what might be worth trying? Delete or rename the config file and run it.
Then you could set the password yourself to AAAAAAAA or BBBBBBBB.
If the encryption is simple code book or rotation ciphers, you'll be able to roll back the original password.
Deleting the configuration file at /home/elf/lab/vending-machines.json and running /home/elf/lab/vending-machines automatically creates a new configuration containing an encrypted password based on input from the user.
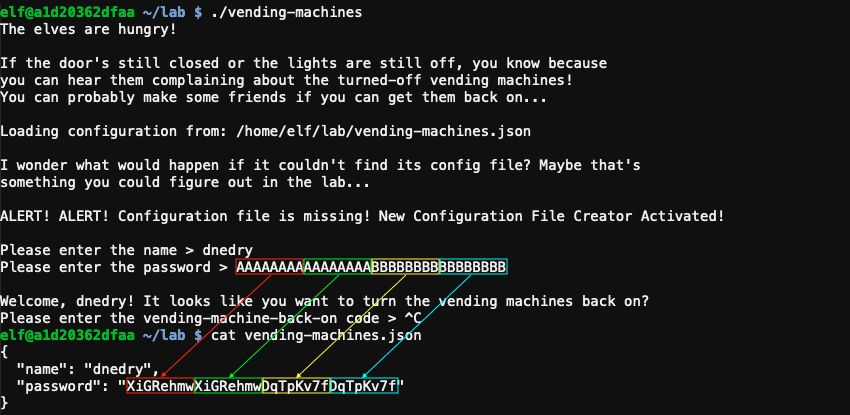
Trial and error tells us that the encrypted value of a character depends on the character's position in the string. The encryption pattern also repeats itself every 8 positions and only letters and numbers are supported. Using create_string.py we can create a string covering all 8 possible positions for each characters and use it as the password when generating a new vending machines configuration. /home/elf/lab/vending-machines.json will contain the encrypted version.
Plaintext
aaaaaaaabbbbbbbbccccccccddddddddeeeeeeeeffffffffgggggggghhhhhhhhiiiiiiii
jjjjjjjjkkkkkkkkllllllllmmmmmmmmnnnnnnnnooooooooppppppppqqqqqqqqrrrrrrrr
ssssssssttttttttuuuuuuuuvvvvvvvvwwwwwwwwxxxxxxxxyyyyyyyyzzzzzzzzAAAAAAAA
BBBBBBBBCCCCCCCCDDDDDDDDEEEEEEEEFFFFFFFFGGGGGGGGHHHHHHHHIIIIIIIIJJJJJJJJ
KKKKKKKKLLLLLLLLMMMMMMMMNNNNNNNNOOOOOOOOPPPPPPPPQQQQQQQQRRRRRRRRSSSSSSSS
TTTTTTTTUUUUUUUUVVVVVVVVWWWWWWWWXXXXXXXXYYYYYYYYZZZZZZZZ0000000011111111
2222222233333333444444445555555566666666777777778888888899999999
Encrypted
9VbtacpgGUVBfWhPe9ee6EERORLdlwWbwcZQAYue8wIUrf5xkyYSPafTnnUgokAhM0sw4eOC
a8okTqy1o63i07r9fm6W7siFqMvusRQJbhE62XDBRjf2h24c1zM5H8XLYfX8vxPy5NAyqmsu
A5PnWSbDcZRCdgTNCujcw9NmuGWzmnRAT7OlJK2X7D7acF1EiL5JQAMUUarKCTZaXiGRehmw
DqTpKv7fLbn3UP9Wyv09iu8Qhxkr3zCnHYNNLCeOSFJGRBvYPBubpHYVzka18jGrEA24nILq
F14D1GnMQKdxFbK363iZBrdjZE8IMJ3ZxlQsZ4Uisdwjup68mSyVX10sI2SHIMBo4gC7VyoG
Np9Tg0akvHBEkVH5t4cXy3VpBslfGtSz0PHMxOl0rQKqjDq2KtqoNicv3ehm9ZFH2rDO5LkI
pWFLz5zSWJ1YbNtlgophDlgKdTzAYdIdjOx0OoJ6JItvtUjtVXmFSQw4lCgPE6x7
Both strings can now be used to decrypt the password by taking each character from the password, finding the 8-character block in Encrypted where this character is located at the same position as in the password, and using the character's overall position in the Encrypted string to retrieve the character at the same location in the Plaintext string. decode_password.py helps to automate this process and decrypts the password stored in /home/elf/vending-machines.json to CandyCane1.
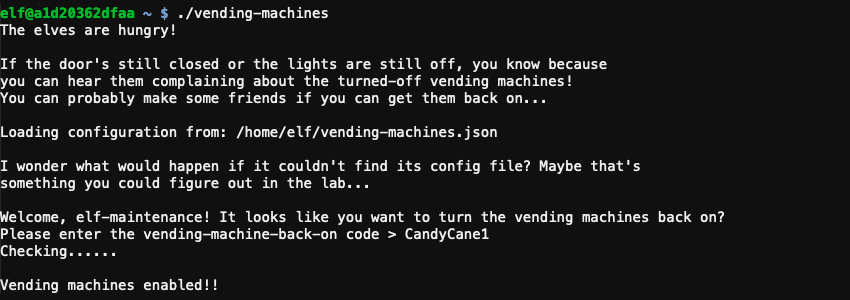
Answer
CandyCane1
Response⚓︎
Bushy Evergreen
Your lookup table worked - great job! That's one way to defeat a polyalphabetic cipher!
Good luck navigating the rest of the castle.
And that Proxmark thing? Some people scan other people's badges and try those codes at locked doors.
Other people scan one or two and just try to vary room numbers.
Do whatever works best for you!