IPv6 Sandbox⚓︎
Elf: Jewel Loggins
Direct link: ipv6 terminal
Objective: Strange USB Device
Request⚓︎
Jewel Loggins
Well hello! I'm Jewel Loggins.
I have to say though, I'm a bit distressed.
The con next door? Oh sure, I'm concerned about that too, but I was talking about the issues I'm having with IPv6.
I mean, I know it's an old protocol now, but I've just never checked it out.
So now I'm trying to do simple things like Nmap and cURL using IPv6, and I can't quite get them working!
Would you mind taking a look for me on this terminal?
I think there's a Github Gist that covers tool usage with IPv6 targets.
The tricky parts are knowing when to use [] around IPv6 addresses and where to specify the source interface.
I've got a deal for you. If you show me how to solve this terminal, I'll provide you with some nice tips about a topic I've been researching a lot lately – Ducky Scripts! They can be really interesting and fun!
Hints⚓︎
IPv6 Reference
Check out this Github Gist with common tools used in an IPv6 context.
Solution⚓︎
Welcome message
Welcome, Kringlecon attendee! The candy striper is running as a service on
this terminal, but I can't remember the password. Like a sticky note under the
keyboard, I put the password on another machine in this network. Problem is: I
don't have the IP address of that other host.
Please do what you can to help me out. Find the other machine, retrieve the
password, and enter it into the Candy Striper in the pane above. I know you
can get it running again!
To find all hosts on the local network, ping the all-nodes (i.e., ff02::1) and all-routers (i.e., ff02::2) multicast addresses (lines 1-2). The latter appears to be optional as ip neigh (line 3) indicates which of the 2 devices is the router regardless. Now that we've identified the non-router host as fe80::42:c0ff:fea8:a002 we can run a port scan against it (line 4). Finally, an HTTP GET request using curl on port 80 tells us that the striper's activation phrase, PieceOnEarth, can be found on TCP port 9000 (lines 5-6).
Terminal commands | |
|---|---|
1 2 3 4 5 6 | |
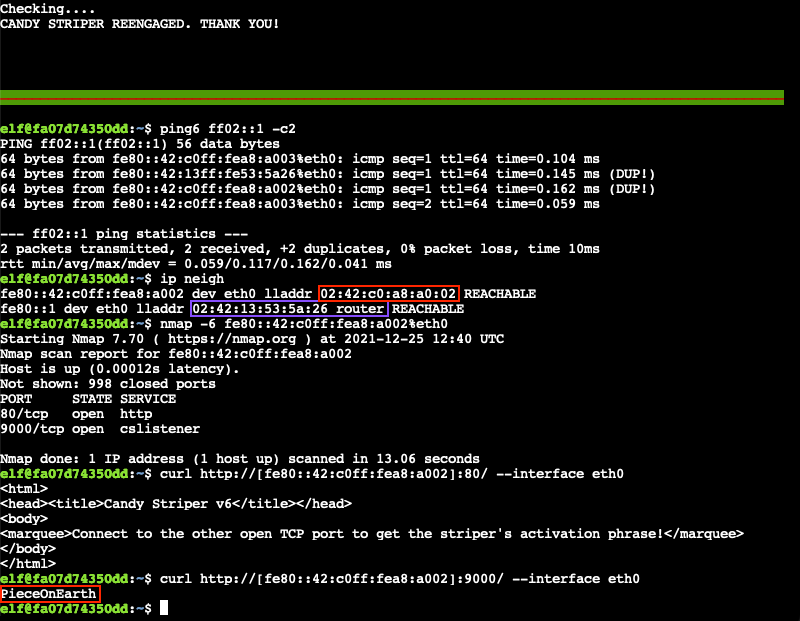
Answer
PieceOnEarth
Response⚓︎
Jewel Loggins
Great work! It seems simpler now that I've seen it once. Thanks for showing me!
Prof. Petabyte warned us about random USB devices. They might be malicious keystroke injectors!
A troll could program a keystroke injector to deliver malicious keystrokes when it is plugged in.
Ducky Script is a language used to specify those keystrokes.
What commands would a troll try to run on our workstations?
I heard that SSH keys can be used as backdoors. Maybe that's useful?