Wireshark Practice⚓︎
Difficulty:
Direct link: Wireshark terminal
Objective⚓︎
Request
Use the Wireshark Phishing terminal in the Tolkien Ring to solve the mysteries around the suspicious PCAP. Get hints for this challenge by typing hint in the upper panel of the terminal.
Sparkle Redberry
Hey there! I’m Sparkle Redberry. We have a bit of an incident here.
We were baking lembanh in preparation for the holidays.
It started to smell a little funky, and then suddenly, a Snowrog crashed through the wall!
We're trying to investigate what caused this, so we can make it go away.
Have you used Wireshark to look at packet capture (PCAP) files before?
I've got a PCAP you might find interesting.
Once you've had a chance to look at it, please open this terminal and answer the questions in the top pane.
Thanks for helping us get to the bottom of this!
Solution⚓︎
Welcome message
This all started when I clicked on a link in my email. Can you help me?
Task: Analyze the Wireshark file and Answer the Elf's Questions!
To complete your task, download the file from your badge or use this command
line to answer the questions.
Tips:
1. Each question may have hints. If you want another hint from the elf, just
type 'hint' in the upper pane.
2. If you need help with Wireshark filters you can go here:
https://wiki.wireshark.org/DisplayFilters
3. If you need help with tshark filters, try this cheat sheet:
https://cheatography.com/mbwalker/cheat-sheets/tshark-wireshark-command-line/
4. Of course, SANS has lots of cheat sheets that can help:
https://www.sans.org/blog/the-ultimate-list-of-sans-cheat-sheets/
5. And remember, you can use Wireshark filters in tshark.
Question 1⚓︎
Question
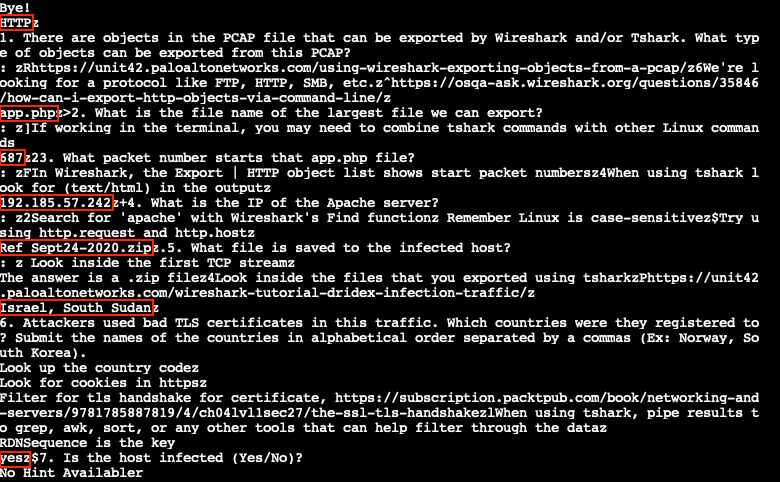
There are objects in the PCAP file that can be exported by Wireshark and/or Tshark. What type of objects can be exported from this PCAP?
Wireshark's File > Export Objects menu lists the different object types that can be exported from the suspicious.pcap file.
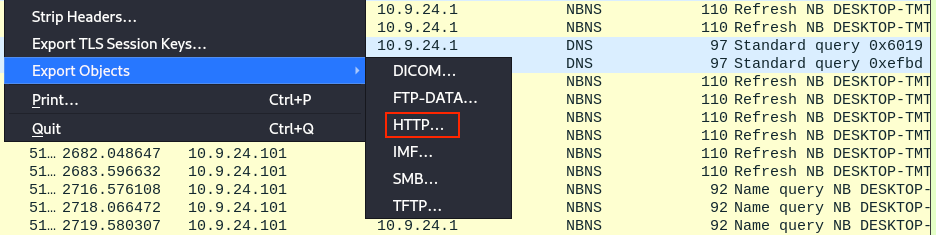
Opening each object type menu entry shows that only the HTTP... submenu leads to several exportable objects.
Answer
http
Question 2⚓︎
Question
What is the file name of the largest file we can export?
The HTTP object list dialog provides the answer to this question. The app.php file is the largest file at 808 Kb.
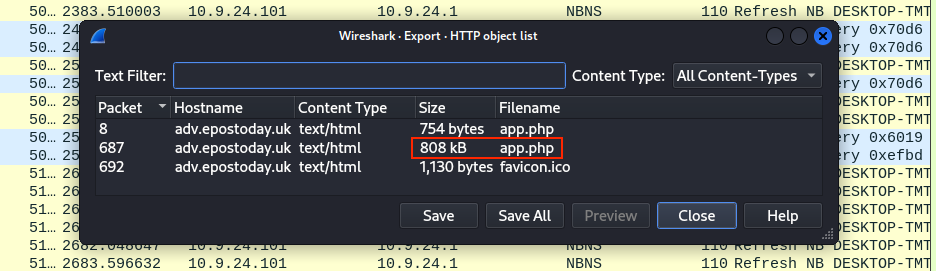
Answer
app.php
Question 3⚓︎
Question
What packet number starts that app.php file?
The answer to this question can again be found in the the HTTP object list dialog, packet 687.
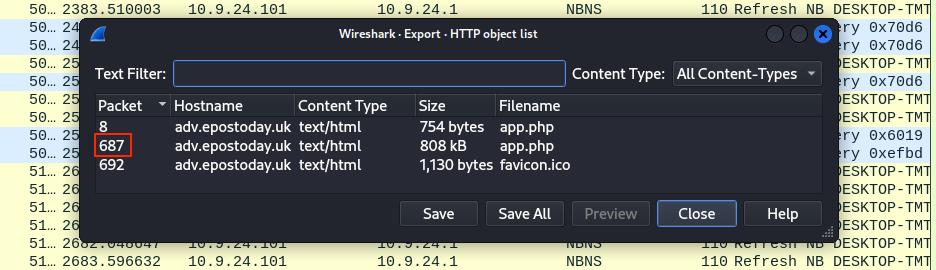
Answer
687
Question 4⚓︎
Question
What is the IP of the Apache server?
Wireshark's HTTP display filter documentation tells us we can use http.server == "Apache" to find the proper IP address.
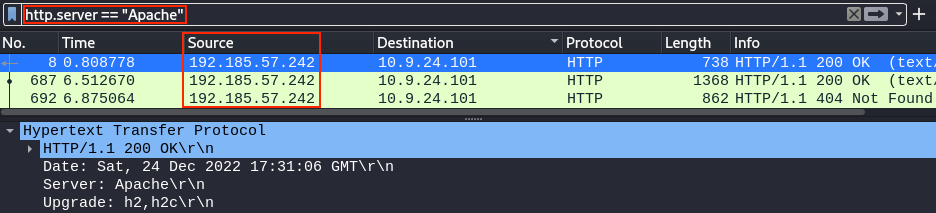
Answer
192.185.57.242
Question 5⚓︎
Question
What file is saved to the infected host?
Exporting the app.php file using the HTTP object list dialog from questions 1 to 3 and looking at the JavaScript code shows a function call on line 68 to a saveAs function which downloads the data stored in blob1 as Ref_Sept24-2020.zip.
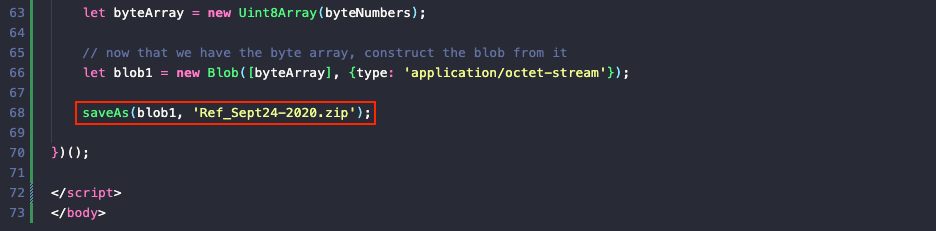
Answer
Ref_Sept24-2020.zip
Question 6⚓︎
Question
Attackers used bad TLS certificates in this traffic. Which countries were they registered to? Submit the names of the countries in alphabetical order separated by a commas (Ex: Norway, South Korea).
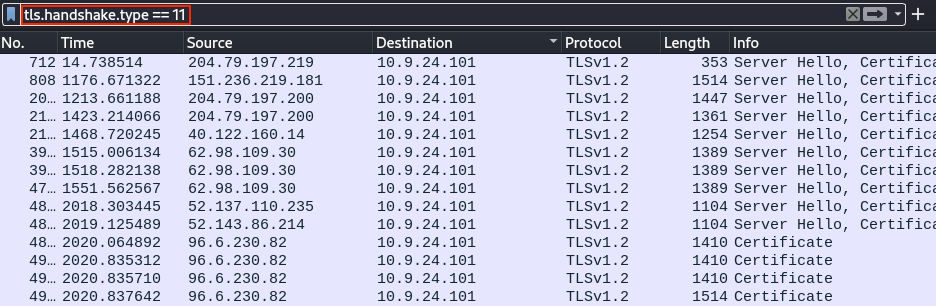
Certificate data is sent as part of TLS handshake packets of type 11. Using tls.handshake.type == 11 we can filter down the list to just those packets that contain certificate details. Selecting each of the packets and reviewing the packet details under the Transport Layer Security and Certificate nodes will tell us country information.
As there's still some legitimate traffic in the filtered packet list, going over every single entry one by one, expanding the nodes, and finding the country code can be tedious. A quicker solution is to find one entry with the proper information, right-clicking on the node and selecting Apply as Column from the context menu.
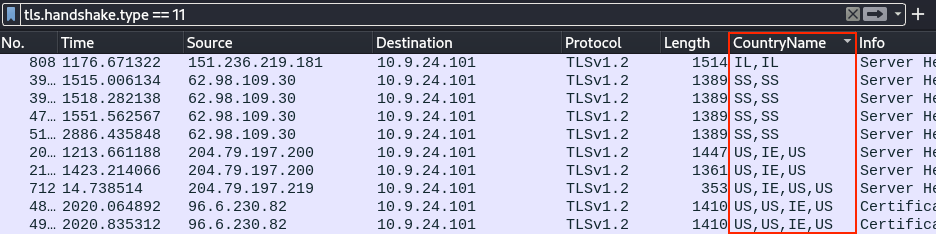
Four countries are found in the certificate data: US, IE, IL, and SS. Inspecting the packet details shows that the US entries belong to Microsoft-issued certificates. The IL (Israel) and SS (South Sudan) entries on the other hand look a lot more suspicious with subject names like heardbellith.Icanwepeh.nagoya and psprponoust.aquarelle.
Answer
Israel, South Sudan
Question 7⚓︎
Question
Is the host infected (Yes/No)?
It sounds like someone fell for a pishing attack. Clicking the link triggered a request for the app.php script after which Ref_Sept24-2020.zip was automatically downloaded. Unpacking Ref_Sept24-2020.zip and executing the embedded malicious Ref_Sept24-2020.scr binary then caused the host to start communicating with the suspicious IL and SS servers.
Since the app.php file contains JavaScript code, we can rename the file to app.html and open it in a web browser in a sandboxed environment. This will trigger the download of the embedded Ref_Sept24-2020.zip file data. Extracting the file, calculating its SHA256 hash using shasum -a 256 Ref_Sept24-2020.scr, and searching for the hash in VirusTotal show that quite a few AntiVirus scanners flag the file as malicious. With analysis results referring to Dridex, this likely is a banking trojan!
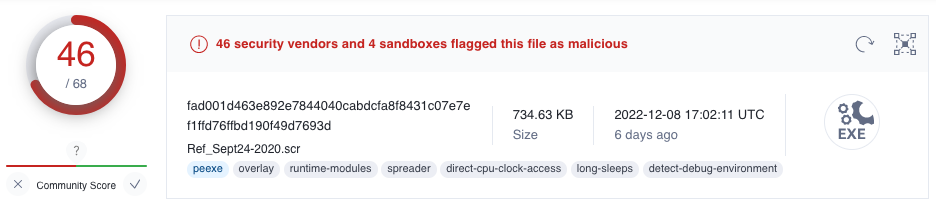
Answer
Yes
Extracting the answers from the /opt/elf binary
If putting in the time and effort to learn about wireshark or tshark isn't your thing, then you're in luck! Someone was nice enough to leave a copy of pyi-archive_viewer in /usr/local/bin which you can use to inspect and extract data from executables created with PyInstaller, like /opt/elf. This binary is run through tmux and is responsible for verifying the answers entered in the top pane.
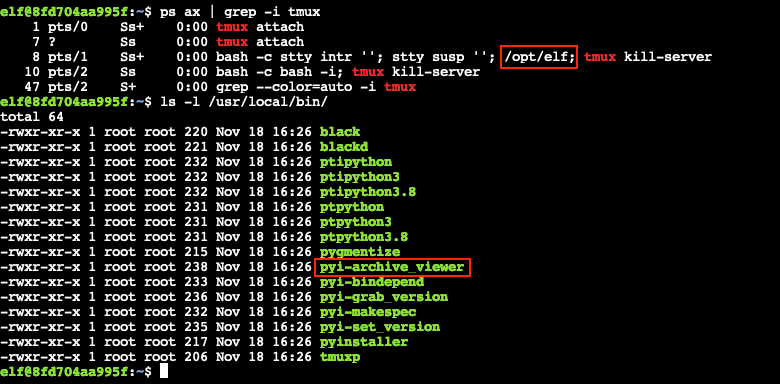
Start by using pyi-archive_viewer /usr/bin/quizme to view all available components in the elf binary.
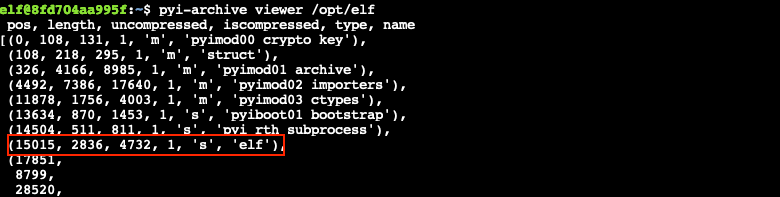
Next, extract the elf component and save it to elf.bin using x elf.
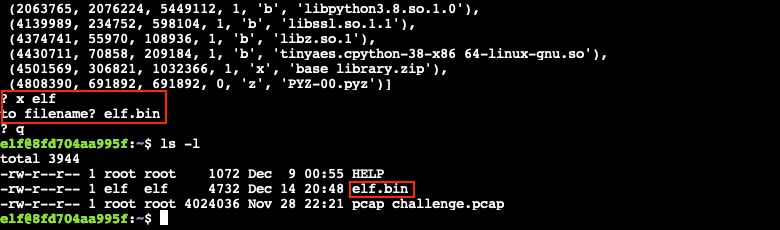
Finally, use strings elf.bin | less to show the answers from the elf.bin file.
Response⚓︎
Sparkle Redberry
You got it - wonderful!
So hey, when you're looking at the next terminal, remember you have multiple filetypes and tools you can utilize.
Conveniently for us, we can use programs already installed on every Windows computer.
So if you brought your own Windows machine, you can save the files to it and use whatever method is your favorite.
Oh yeah! If you wanna learn more, or get stuck, I hear Eric Pursley's talk is about this very topic.